Security practitioners for decades have advised people to limit DNS queries against their DNS servers to only use UDP port 53. The reality is that DNS queries can also use TCP port 53 if UDP port 53 is not accepted. Now with the impending deployment of DNSSEC and the eventual addition of IPv6 we will need to allow our firewalls for forward both TCP and UDP port 53 packets.
DNS can be used by attackers as one of their reconnaissance techniques. Public information contained a target's servers is valuable to an attacker and helps them focus their attacks. Attackers can use a variety of techniques to retrieve DNS information through queries. However, hackers often try to perform a zone transfer from your authoritative DNS servers to gain access to even more information.
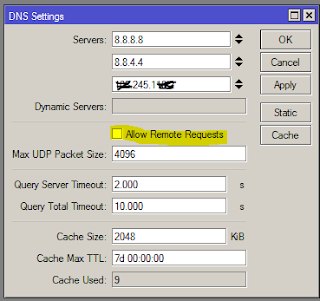
Do not check mark Allow Remote Requests
/ip firewall filter add chain=input action=drop in-interface=e
ther1 src-address=0.0.0.0/0 dst-port=53 protocol=udp comment="Securing DNS udp"
/ip firewall filter add chain=input action=drop in-interface=ether1 src-address=0.0.0.0/0 dst-port=53 protocol=tcp comment="Securing DNS tcp"
DNS can be used by attackers as one of their reconnaissance techniques. Public information contained a target's servers is valuable to an attacker and helps them focus their attacks. Attackers can use a variety of techniques to retrieve DNS information through queries. However, hackers often try to perform a zone transfer from your authoritative DNS servers to gain access to even more information.
Do not check mark Allow Remote Requests
/ip firewall filter add chain=input action=drop in-interface=e
ther1 src-address=0.0.0.0/0 dst-port=53 protocol=udp comment="Securing DNS udp"
/ip firewall filter add chain=input action=drop in-interface=ether1 src-address=0.0.0.0/0 dst-port=53 protocol=tcp comment="Securing DNS tcp"
No comments:
Post a Comment